Cyber Security
Cyber Security
Cyber Security
Firewalls
Firewalls act as a barrier between a trusted internal network and untrusted external networks, such as the internet. They control incoming and outgoing network traffic based on predetermined security rules.
Antivirus Software
Antivirus software detects and removes malicious software, such as viruses, worms, and trojans, from computer systems. It continuously scans files and programs to prevent infections and ensure system integrity.
Encryption
Encryption converts data into a code that can only be deciphered with the appropriate encryption key. It protects sensitive information during transmission and storage, making it unreadable to unauthorized users.
Patch Management
Patch management involves regularly updating software and systems with the latest security patches and fixes to address vulnerabilities and protect against known exploits.
Security Awareness Training
Educating employees and users about cybersecurity best practices and potential threats is crucial for preventing social engineering attacks, such as phishing and pretexting.
Security Audits and Risk Assessments
Regular security audits and risk assessments help organizations identify vulnerabilities, assess their risk exposure, and prioritize cybersecurity investments and actions.
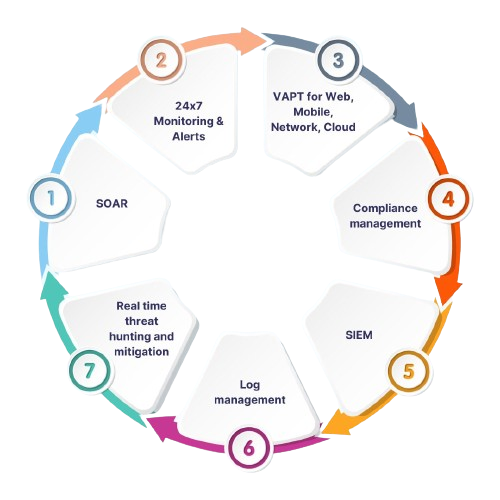
Cyber Security Service
Cyber Security Service
Cybersecurity Service provides comprehensive protection against digital threats, safeguarding sensitive data, networks, and systems from cyberattacks. Leveraging advanced technologies and expertise, these services offer a range of solutions including threat detection, incident response, vulnerability assessments, and security consulting. By implementing firewalls, encryption, antivirus software, and other defense mechanisms, they mitigate risks posed by malware, ransomware, phishing, and other cyber threats.
Cyber SecuritySupport
Cyber Security Support
Cyber Security Support offers expert assistance in safeguarding digital assets against cyber threats. This service provides proactive monitoring, incident response, and resolution to mitigate risks and ensure the resilience of organizational infrastructure. Skilled professionals offer guidance in implementing security measures such as firewalls, encryption, and access controls, tailored to specific needs and compliance requirements. Cyber Security Support also includes timely updates, patch management, and continuous monitoring to stay ahead of emerging threats.

Frequently asked
questions about
Cyber Security
Cybersecurity encompasses the practices, technologies, and processes designed to protect digital systems, networks, devices, and data from unauthorized access, misuse, alteration, or destruction. It involves defending against a wide range of cyber threats, including malware, ransomware, phishing attacks, data breaches, and other forms of cybercrime.
Cybersecurity is essential for protecting sensitive data, preserving trust, ensuring compliance, maintaining business continuity, mitigating threats, safeguarding intellectual property, and ensuring national security. With the rise of digital threats, robust cybersecurity measures are crucial for organizations and individuals to stay secure in the digital age.
The work process of cybersecurity involves several key steps: first, identifying and assessing potential threats and vulnerabilities; second, implementing security measures such as firewalls, encryption, and access controls; third, continuously monitoring networks and systems for suspicious activity; fourth, promptly detecting and responding to security incidents; fifth, mitigating the impact of incidents through incident response and recovery procedures; and finally, regularly reviewing and updating security measures to adapt to evolving threats. This iterative process aims to protect digital assets, maintain business operations, and minimize the risk of cyberattacks and data breaches.
